TryHackMe之PreSecurity
1 | 本来想来打打tryhackme的靶机,结果被hackpath种草了 |
Pre Security
Introduction to Cyber Security
Offensive Security Intro
1 | Which of the following options better represents the process where you simulate a hacker's actions to find vulnerabilities in a system? |
1 | gobuster -u http://fakebank.thm -w wordlist.txt dir |
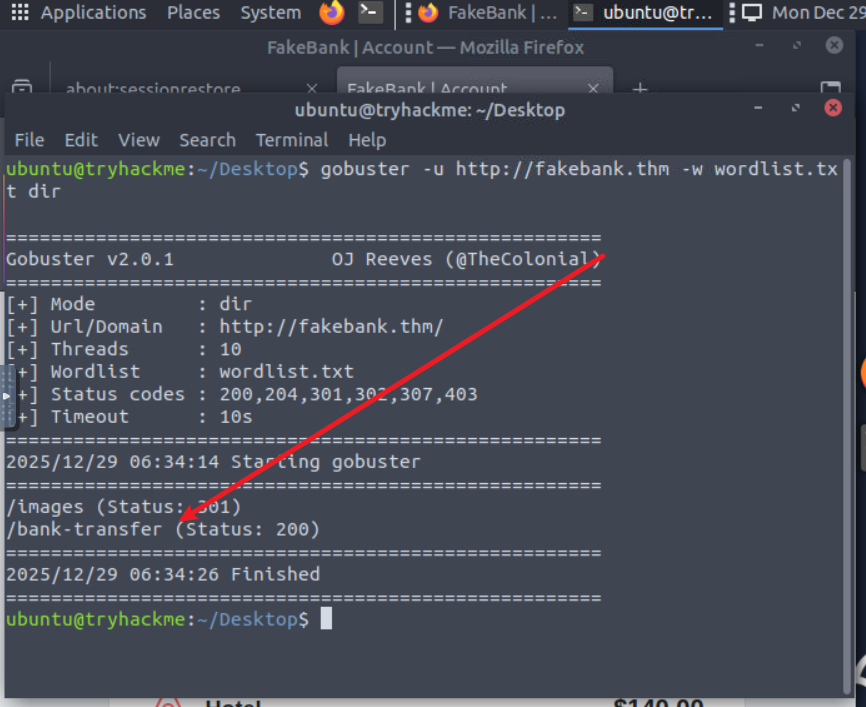
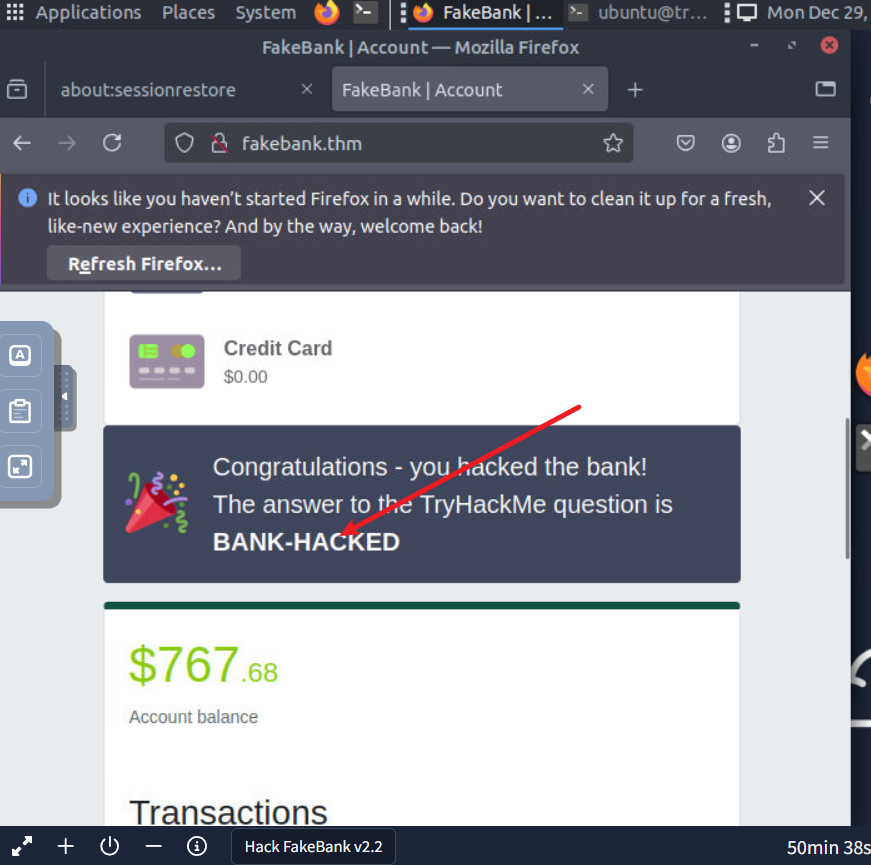
1 | 根据情景输入即可 |
Defensive Security Intro
1 | Which team focuses on defensive security? |
1 | What would you call a team of cyber security professionals that monitors a network and its systems for malicious events? |
1 | 根据操作来就行比较简单,注意空格 |
Careers in Cyber
Security Analyst
1 | Security analysts are integral to constructing security measures across organisations to protect the company from attacks. Analysts explore and evaluate company networks to uncover actionable data and recommendations for engineers to develop preventative measures. This job role requires working with various stakeholders to gain an understanding of security requirements and the security landscape. |
Security Engineer
1 | Security engineers develop and implement security solutions using threats and vulnerability data - often sourced from members of the security workforce. Security engineers work across circumventing a breadth of attacks, including web application attacks, network threats, and evolving trends and tactics. The ultimate goal is to retain and adopt security measures to mitigate the risk of attack and data loss. |
Incident Responder
1 | Incident responders respond productively and efficiently to security breaches. Responsibilities include creating plans, policies, and protocols for organisations to enact during and following incidents. This is often a highly pressurised position with assessments and responses required in real-time, as attacks are unfolding. Incident response metrics include MTTD, MTTA, and MTTR - the meantime to detect, acknowledge, and recover (from attacks.) The aim is to achieve a swift and effective response, retain financial standing and avoid negative breach implications. Ultimately, incident responders protect the company's data, reputation, and financial standing from cyber attacks. |
Digital Forensics Examiner
1 | If you like to play detective, this might be the perfect job. If you are working as part of a law-enforcement department, you would be focused on collecting and analysing evidence to help solve crimes: charging the guilty and exonerating the innocent. On the other hand, if your work falls under defending a company's network, you will be using your forensic skills to analyse incidents, such as policy violations. |
Malware Analyst
1 | A malware analyst's work involves analysing suspicious programs, discovering what they do and writing reports about their findings. A malware analyst is sometimes called a reverse-engineer as their core task revolves around converting compiled programs from machine language to readable code, usually in a low-level language. This work requires the malware analyst to have a strong programming background, especially in low-level languages such as assembly language and C language. The ultimate goal is to learn about all the activities that a malicious program carries out, find out how to detect it and report it. |
Penetration Tester
1 | You may see penetration testing referred to as pentesting and ethical hacking. A penetration tester's job role is to test the security of the systems and software within a company - this is achieved through attempts to uncover flaws and vulnerabilities through systemised hacking. Penetration testers exploit these vulnerabilities to evaluate the risk in each instance. The company can then take these insights to rectify issues to prevent a real-world cyberattack. |
Red Teamer
1 | Red teamers share similarities to penetration testers, with a more targeted job role. Penetration testers look to uncover many vulnerabilities across systems to keep cyber-defence in good standing, whilst red teamers are enacted to test the company's detection and response capabilities. This job role requires imitating cyber criminals' actions, emulating malicious attacks, retaining access, and avoiding detection. Red team assessments can run for up to a month, typically by a team external to the company. They are often best suited to organisations with mature security programs in place. |
Network Fundamentals
What is Networking
What is Networking
1 | What is the key term for devices that are connected together? |
What is the Internet?
1 | Who invented the World Wide Web? |
Identifying Devices on a Network
1 | What does the term "IP" stand for? |
Ping (ICMP)
1 | What protocol does ping use? |
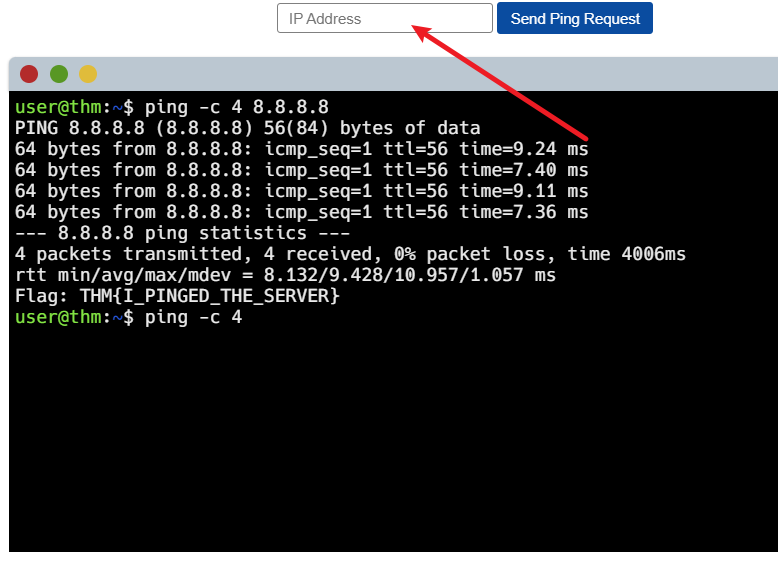
Intro to LAN
Introducing LAN Topologies
1 | What does LAN stand for? |
A Primer on Subnetting
1 | What is the technical term for dividing a network up into smaller pieces? |
ARP
1 | What does ARP stand for? |
DHCP
1 | What type of DHCP packet is used by a device to retrieve an IP address? |
OSI Model
What is the OSI Model?
1 | What does the "OSI" in "OSI Model" stand for? |
Layer 1 - Physical
1 | What is the name of this Layer? |
Layer 2 - Data Link
1 | What is the name of this Layer? |
Layer 3 - Network
1 | What is the name of this Layer? |
Layer 4 - Transport
1 | What is the name of this Layer? |
Layer 5 - Session
1 | What is the name of this layer? |
Layer 6 - Presentation
1 | What is the name of this Layer? |
Layer 7 - Application
1 | What is the name of this Layer? |
Packets & Frames
What are Packets and Frames
1 | What is the name for a piece of data when it does have IP addressing information? |
TCP/IP (The Three-Way Handshake)
1 | What is the header in a TCP packet that ensures the integrity of data? |
UDP/IP
1 | What does the term "UDP" stand for? |
Extending Your Network
Introduction to Port Forwarding
1 | What is the name of the device that is used to configure port forwarding? |
Firewalls 101
1 | What layers of the OSI model do firewalls operate at? |
VPN Basics
1 | What VPN technology only encrypts & provides the authentication of data? |
LAN Networking Devices
1 | What is the verb for the action that a router does? |
How The Web Works
DNS in Detail
What is DNS?
1 | What does DNS stand for? |
Domain Hierarchy
1 | What is the maximum length of a subdomain? |
Record Types
1 | What type of record would be used to advise where to send email? |
Making A Request
1 | What field specifies how long a DNS record should be cached for? |
HTTP in Detail
What is HTTP(S)?
1 | What does HTTP stand for? |
Requests And Responses
1 | What HTTP protocol is being used in the above example? |
HTTP Methods
1 | What method would be used to create a new user account? |
HTTP Status Codes
1 | What response code might you receive if you've created a new user or blog post article? |
HTTPHeaders
1 | What header tells the web server what browser is being used? |
Cookies
1 | Which header is used to save cookies to your computer? |
How Websites Work
How websites work
1 | What term best describes the component of a web application rendered by your browser? |
HTML
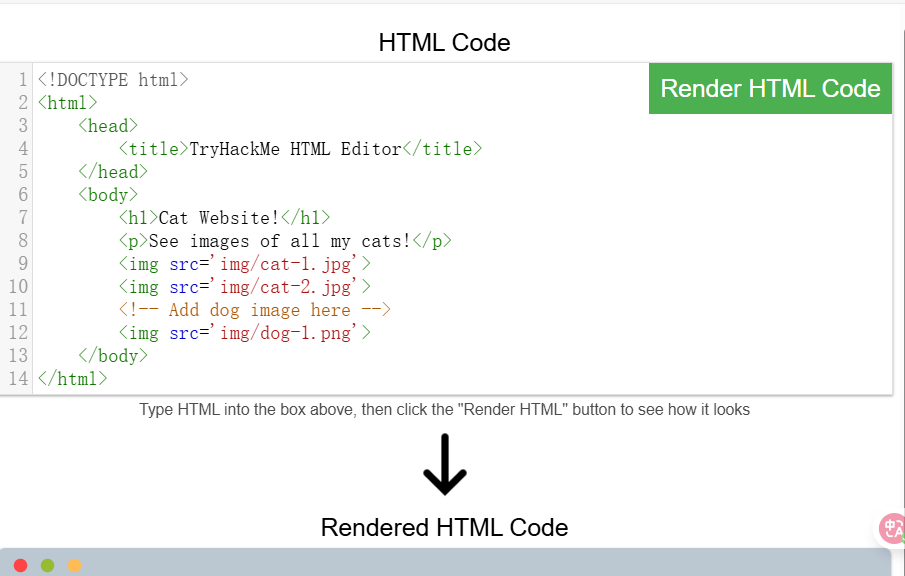
JavaScript
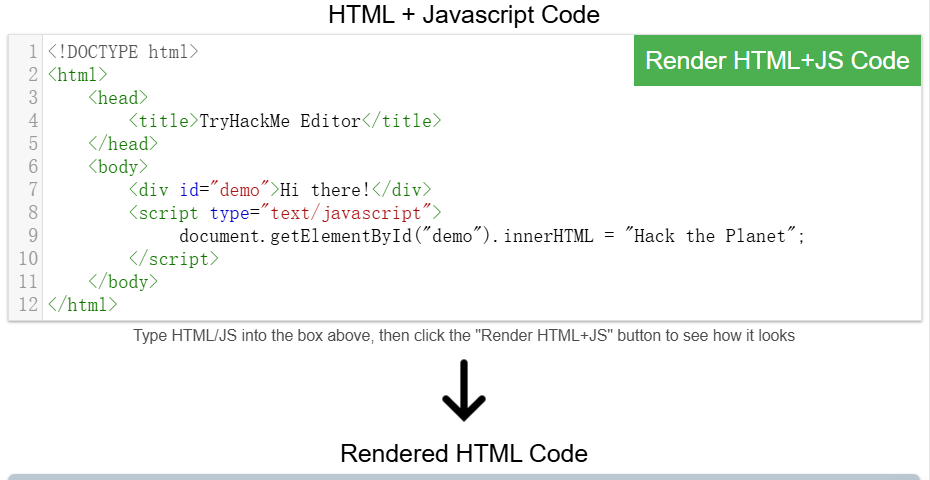
Sensitive Data Exposure
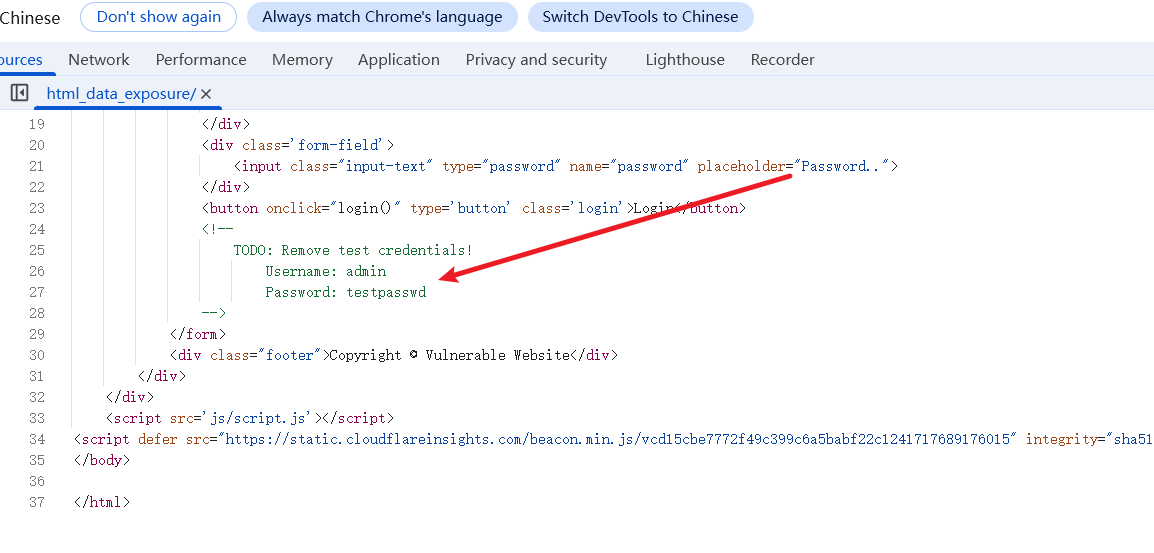
HTML Injection
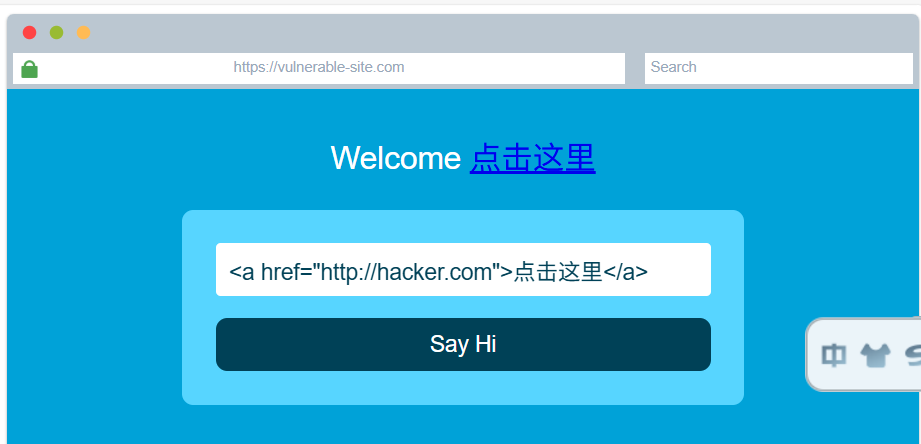
Putting it all together
Other Components
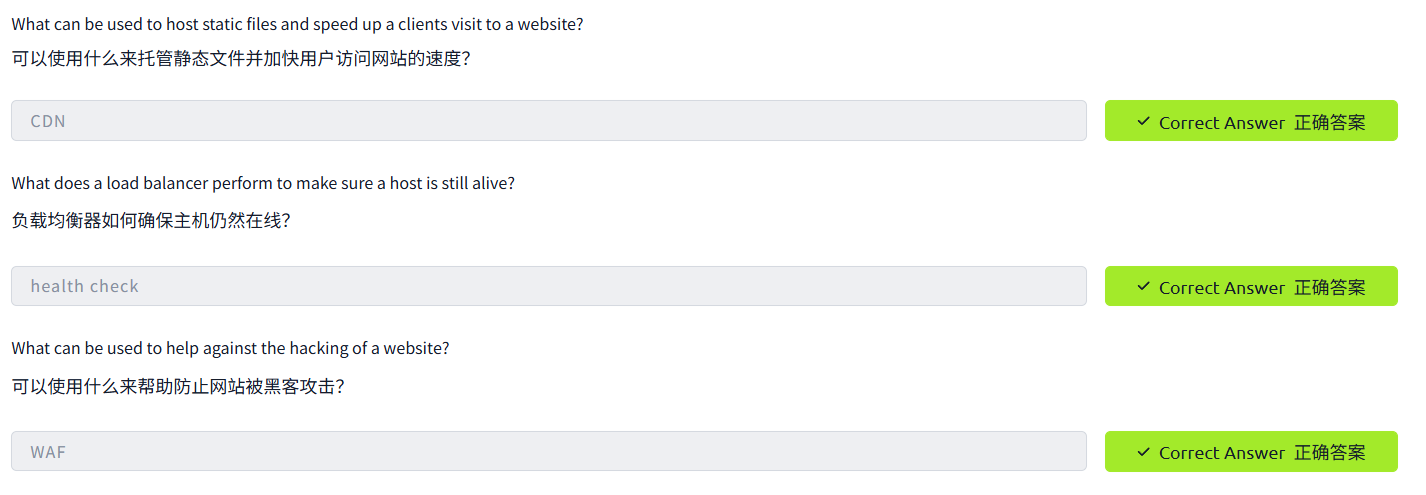
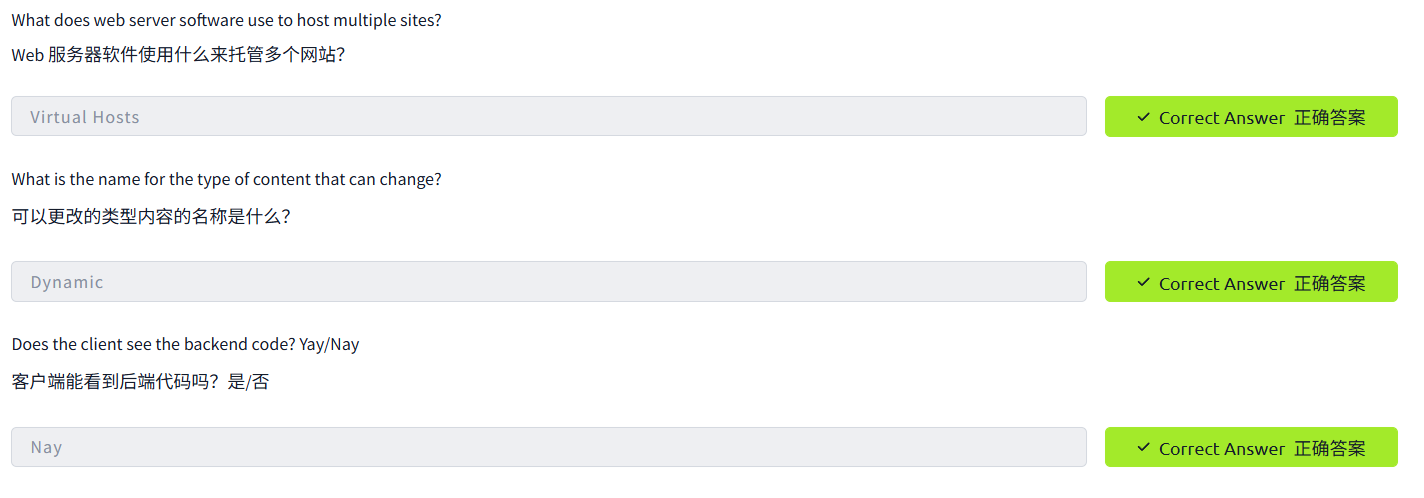
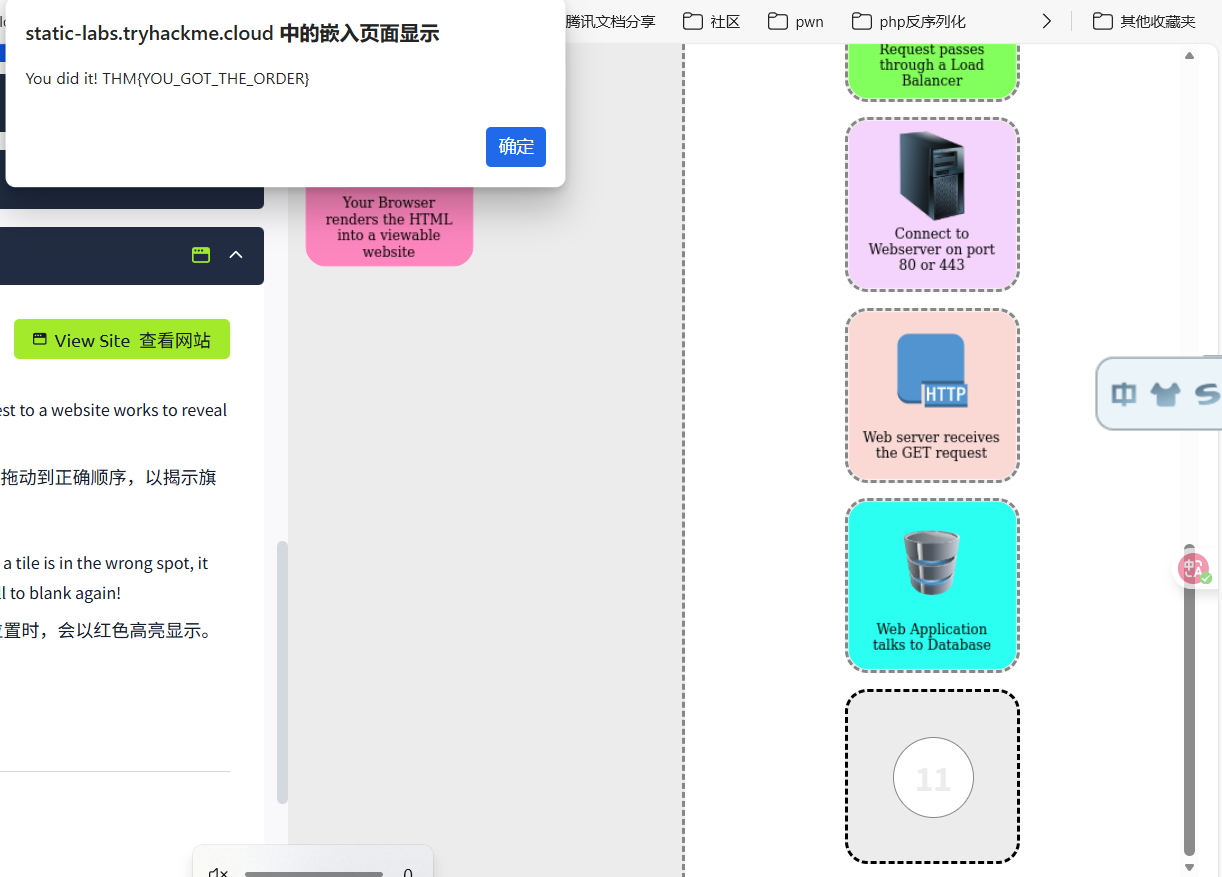
How Web Servers Work
quiz
Linux Fundamentals
Linux Fundamentals Part 1
Running Your First few Commands
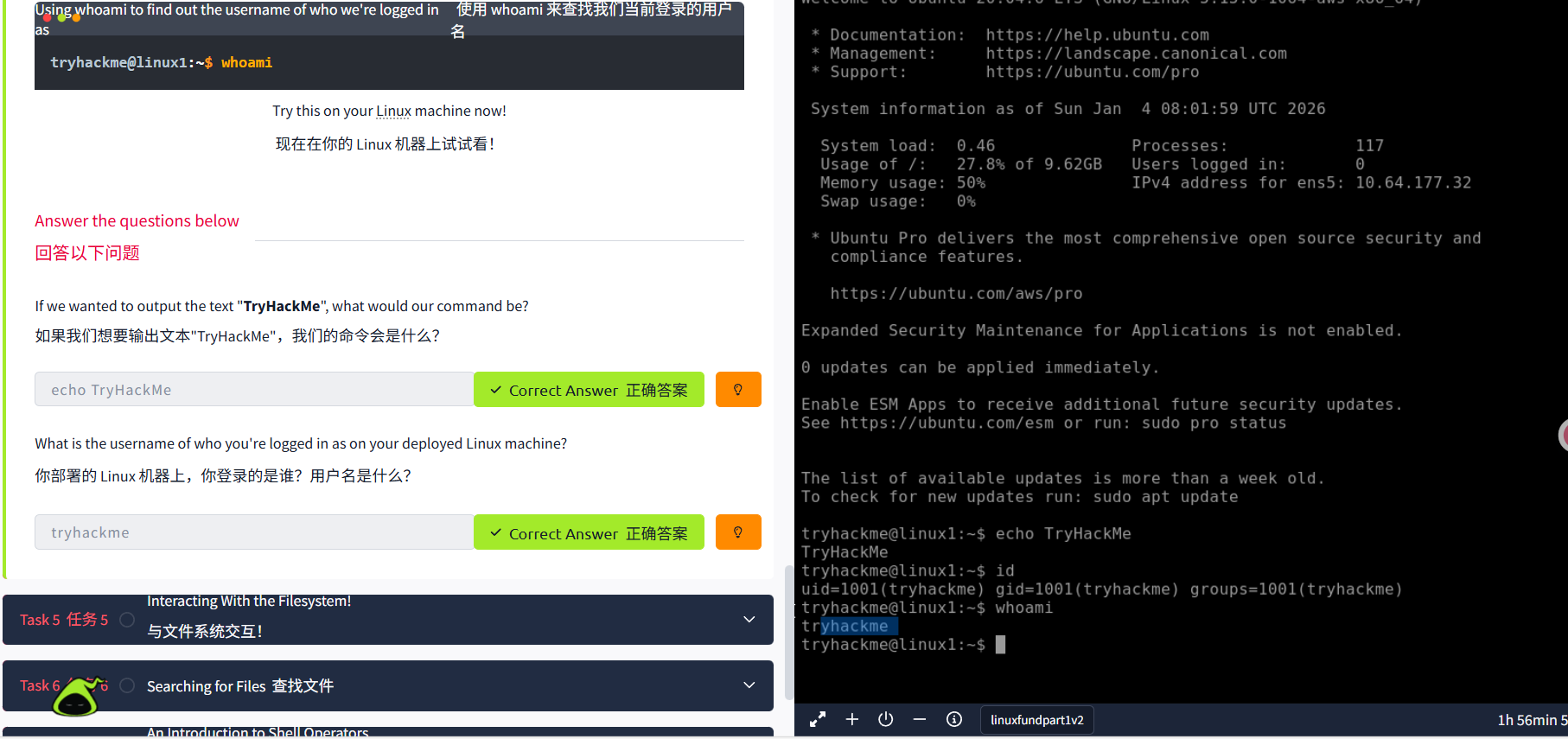
Interacting With the Filesystem!
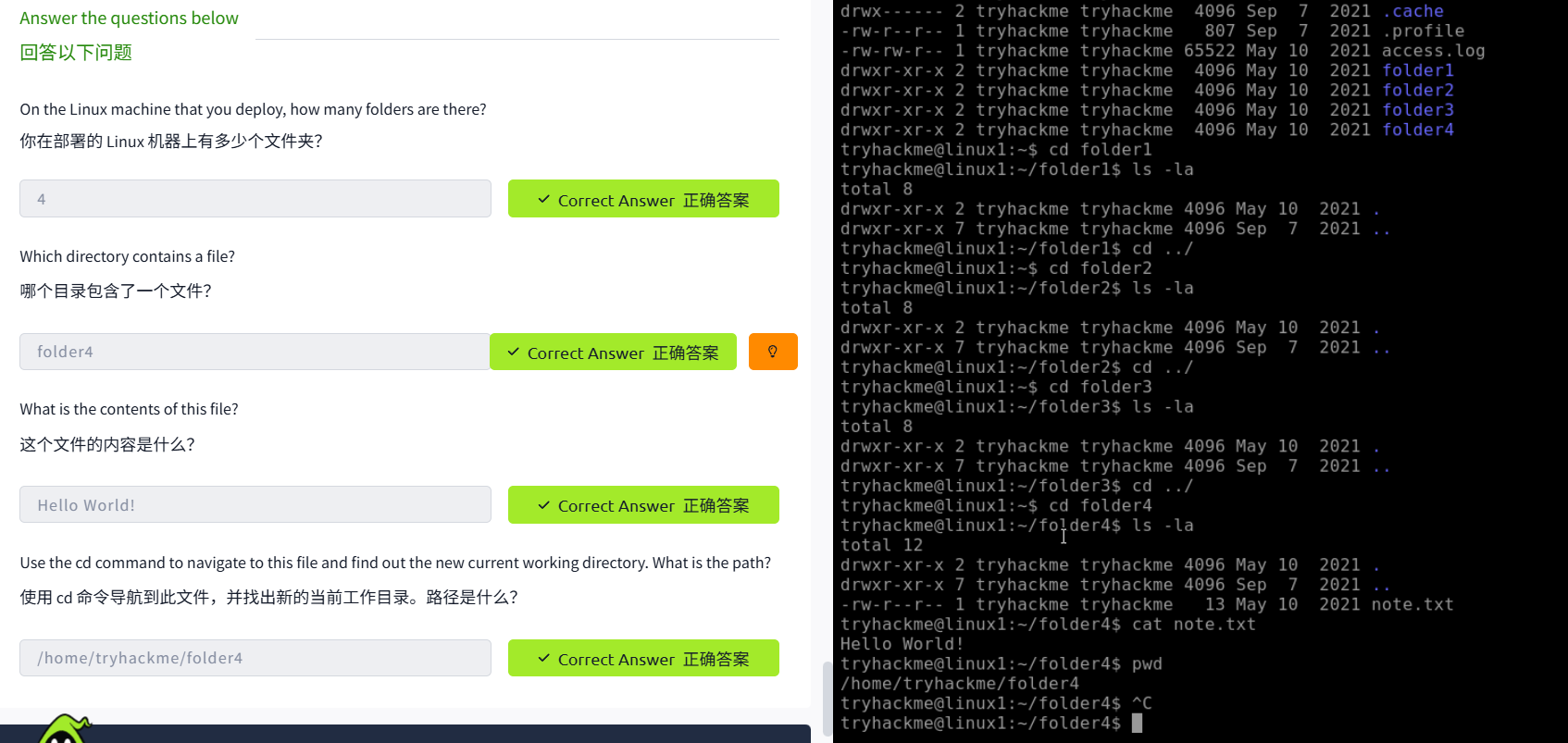
Searching for Files
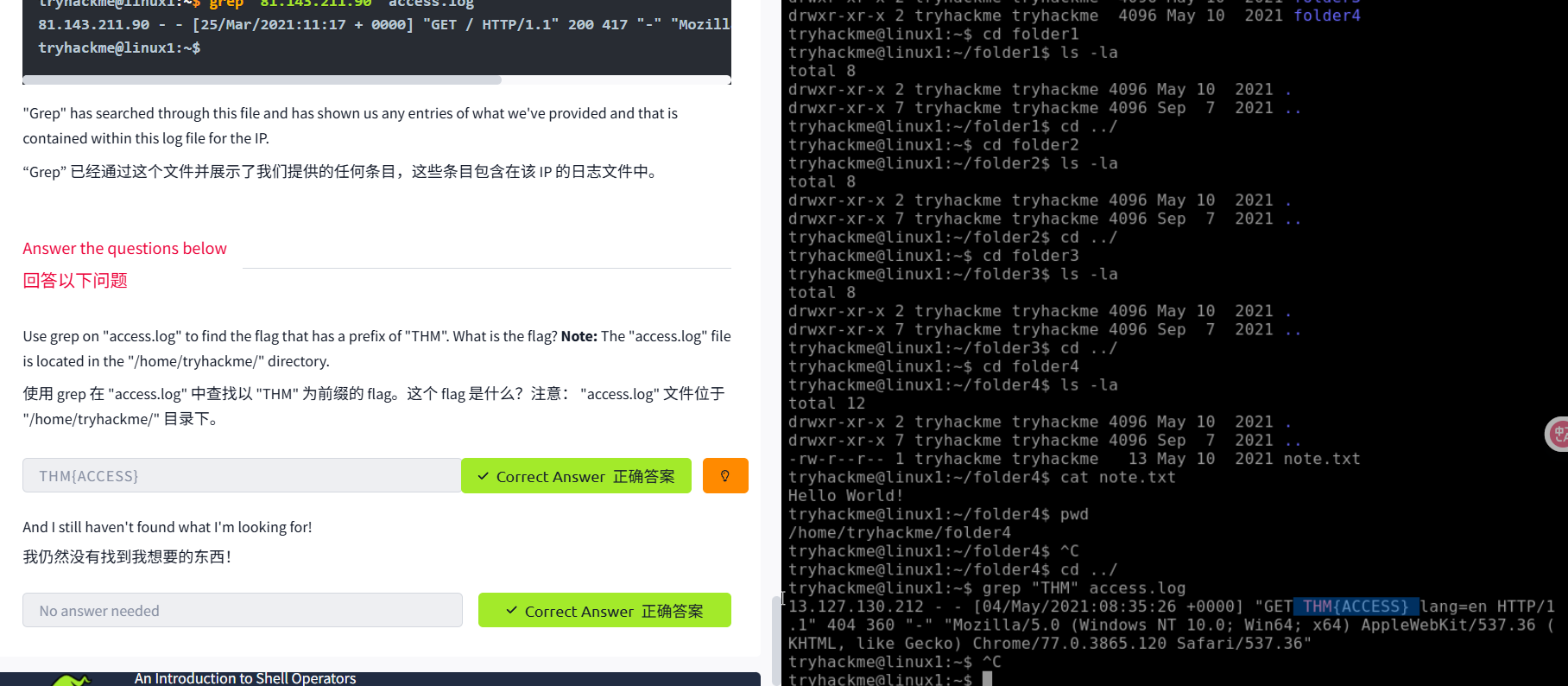
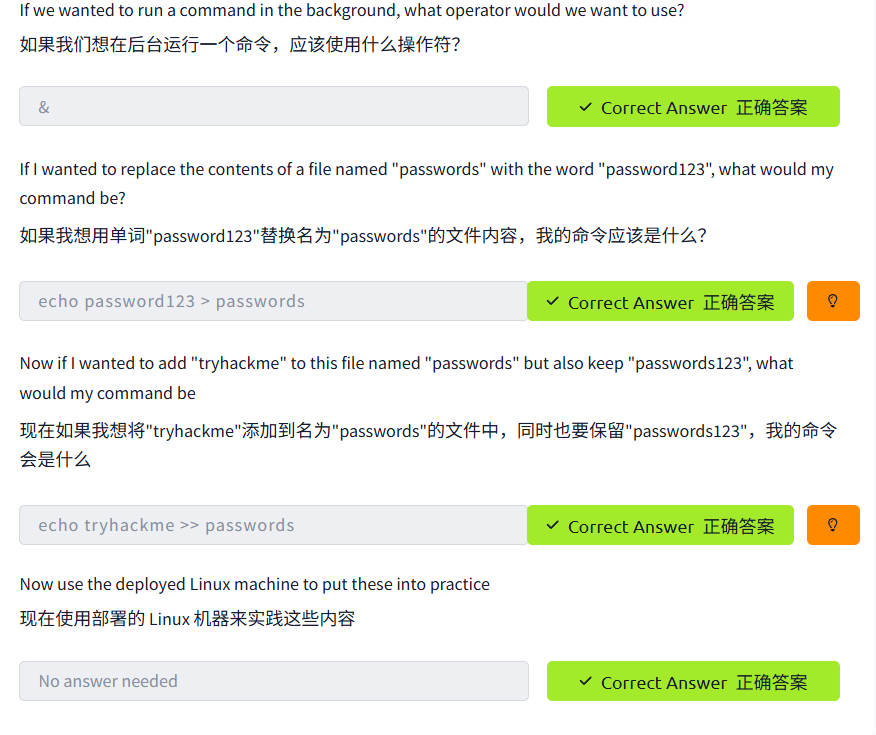
An Introduction to Shell Operators
Linux Fundamentals Part 2
Introduction to Flags and Switches
Filesystem Interaction Continued
Permissions 101
Common Directories
Linux Fundamentals Part 3
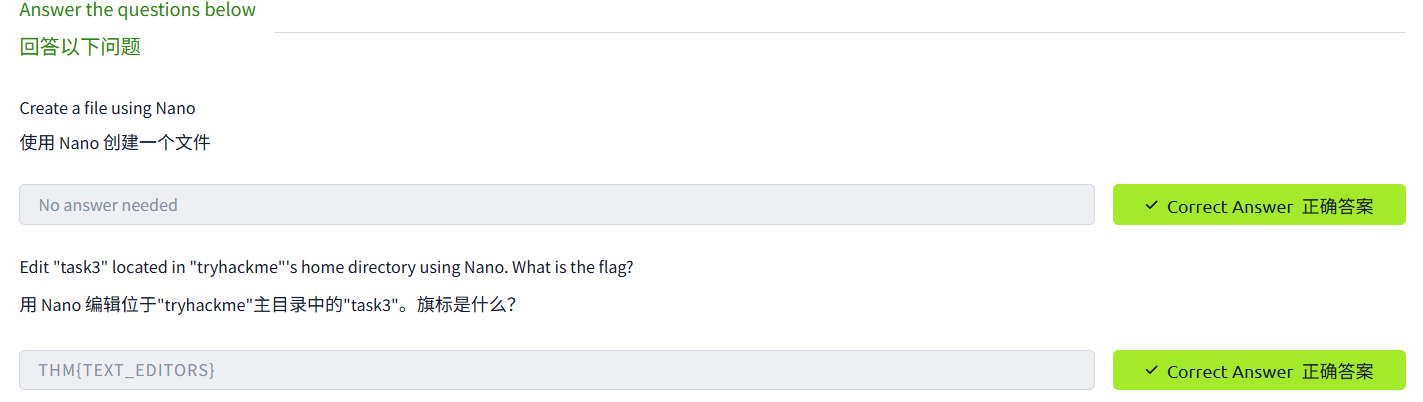
Terminal Text Editors
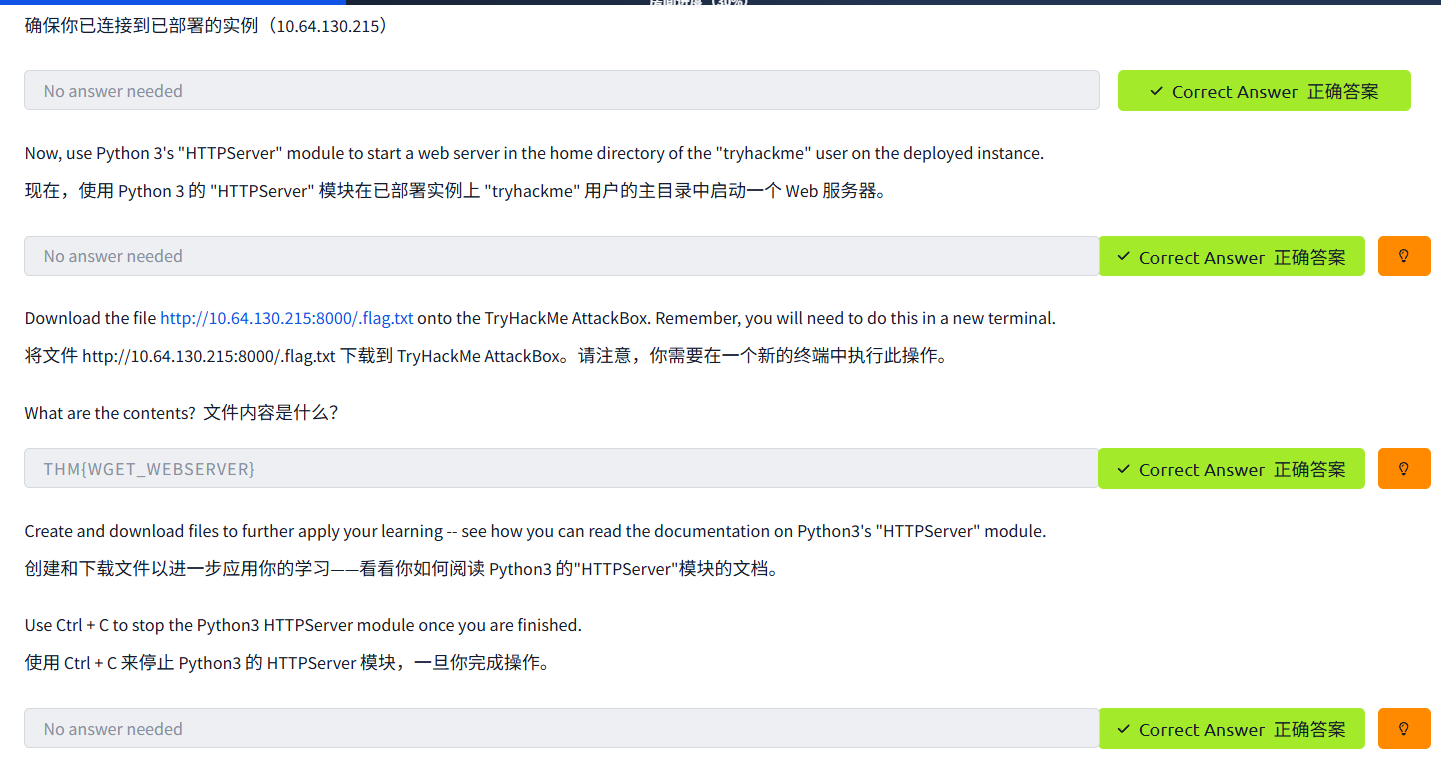
General/Useful Utilities
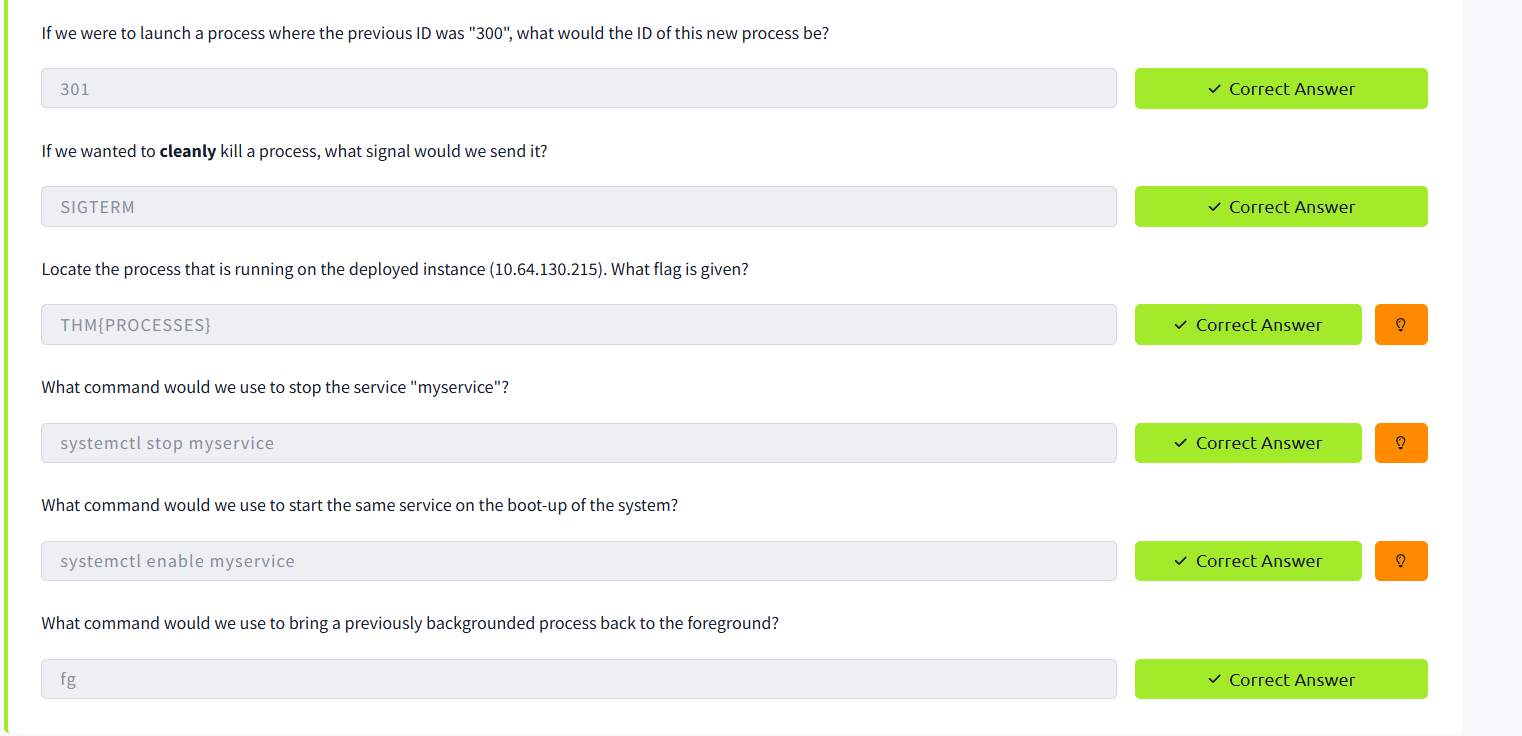
Processes 101
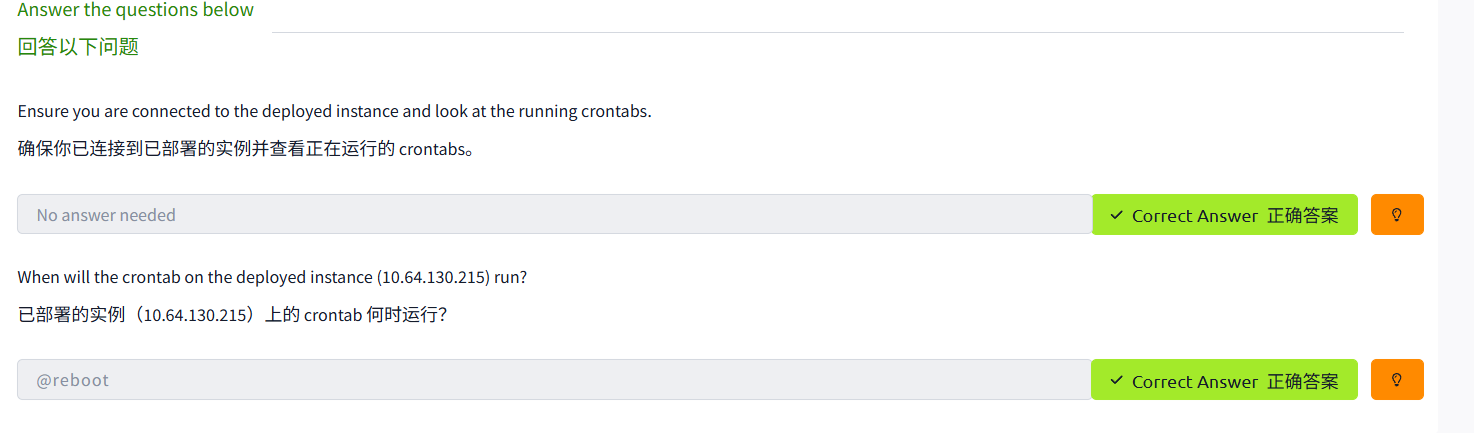
Maintaining Your System: Automation
ManagementMaintaining Your System: Logs
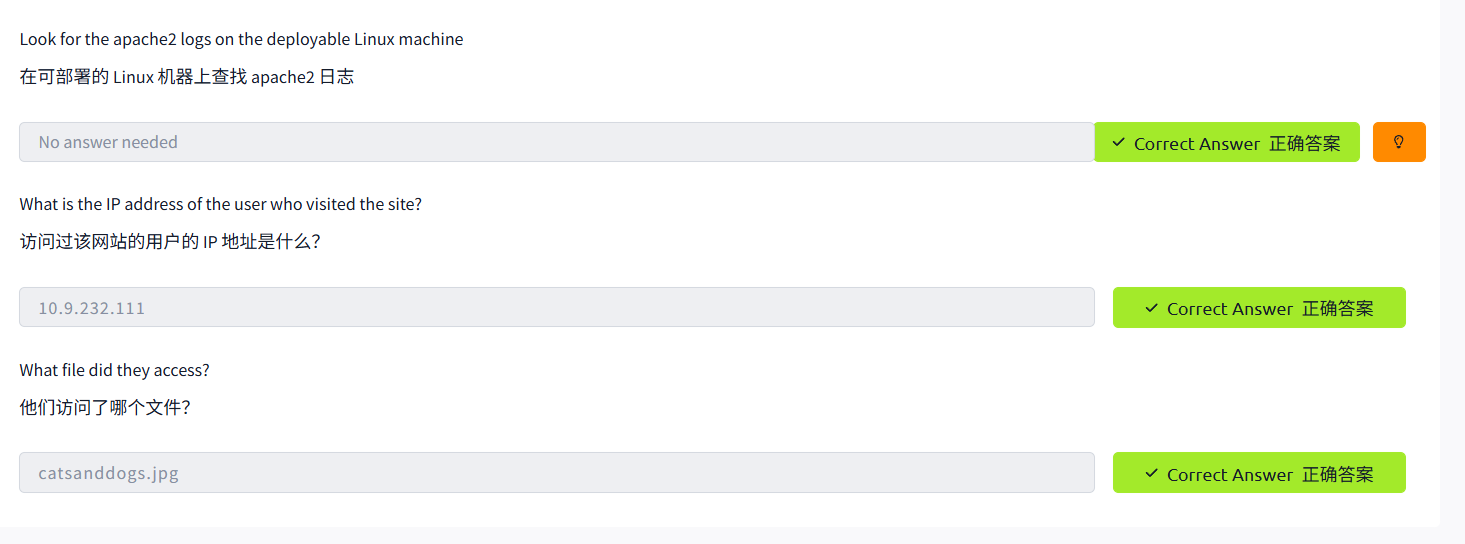
Windows Fundamentals
Windows Fundamentals 1
The File System 文件系统
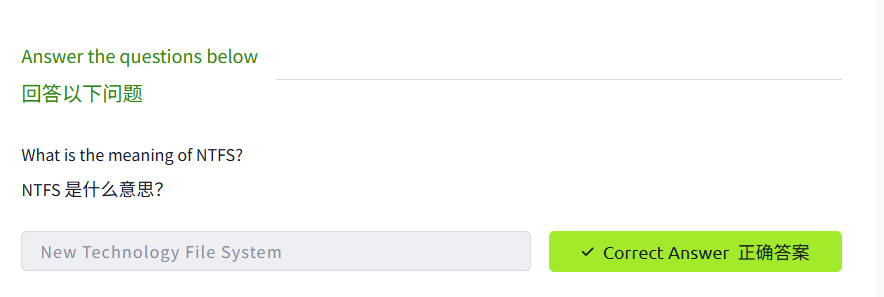
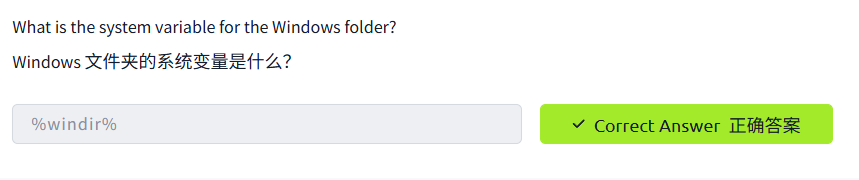
The Windows\System32 Folders
User Accounts, Profiles, and Permissions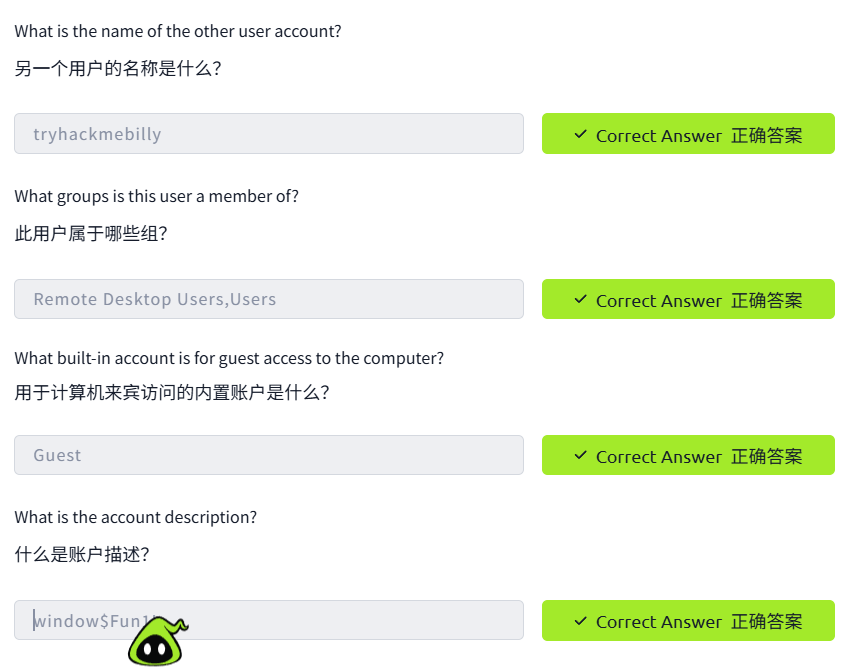
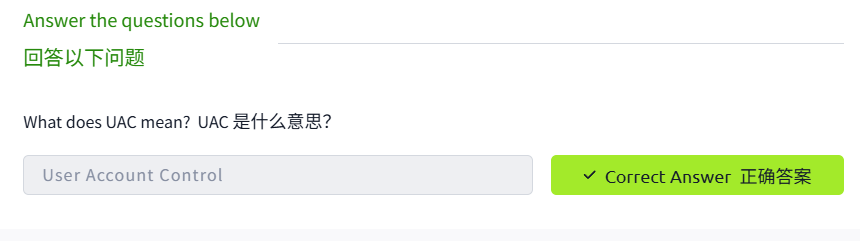
User Account Control
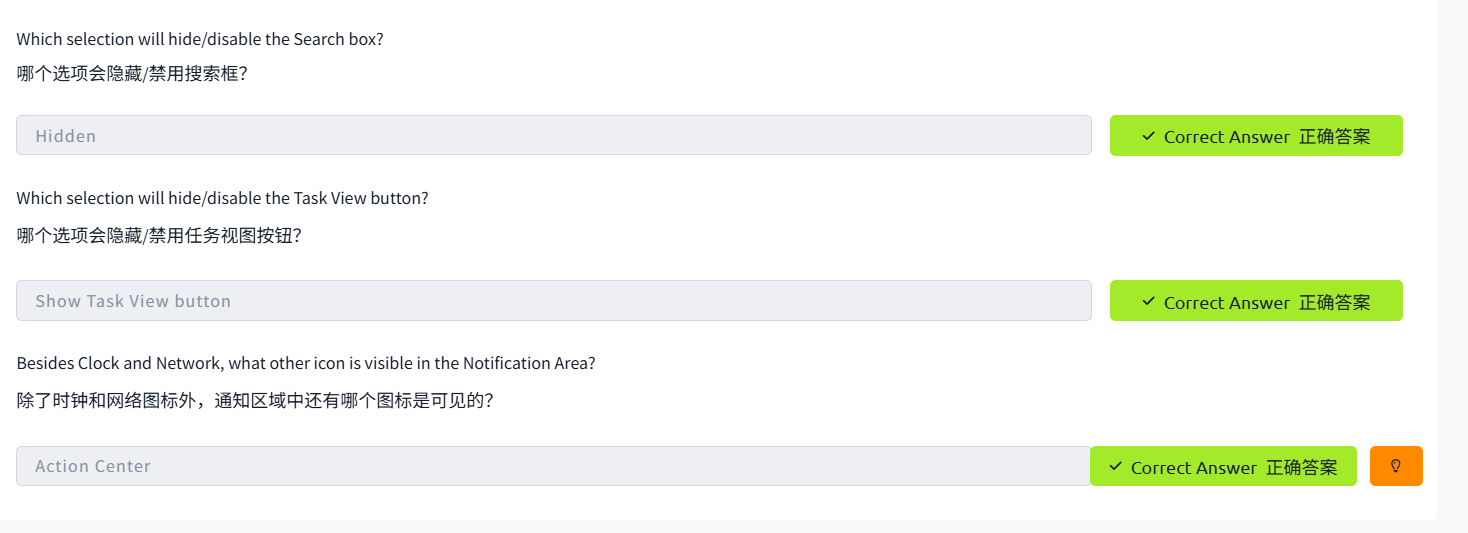
The Desktop (GUI)
Windows Fundamentals 2
System Configuration and Advanced System Settings
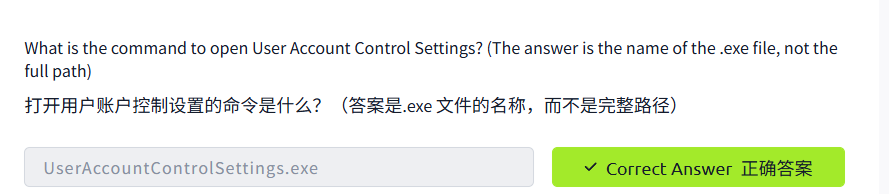
Change UAC Settings
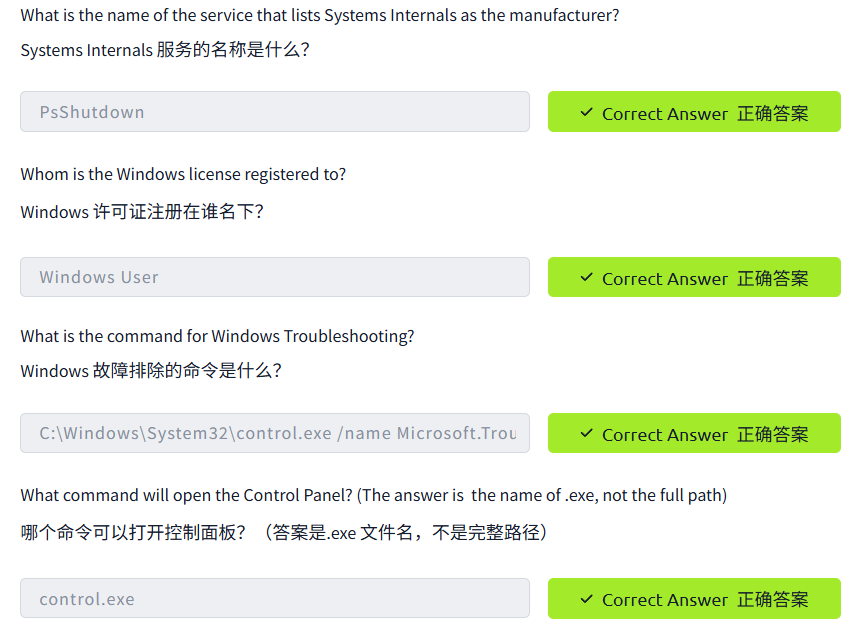
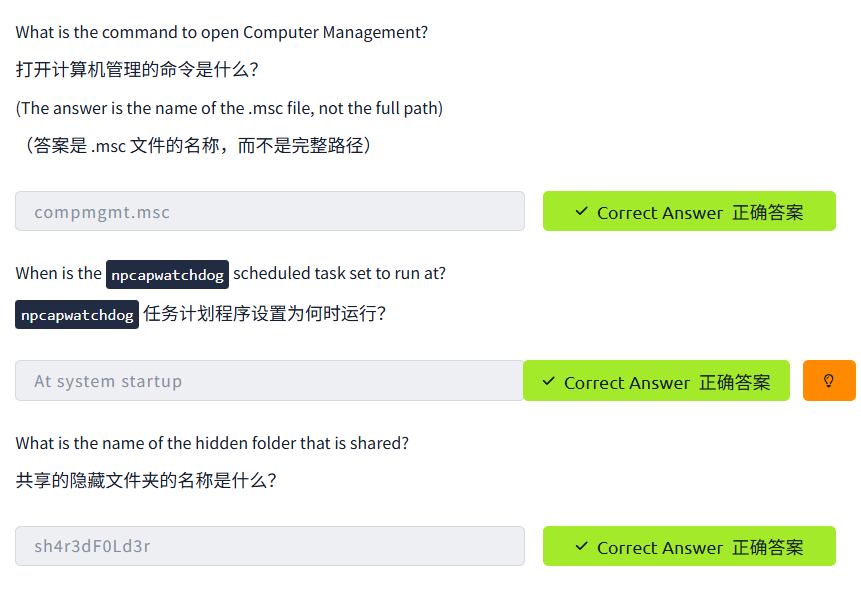
Computer Management
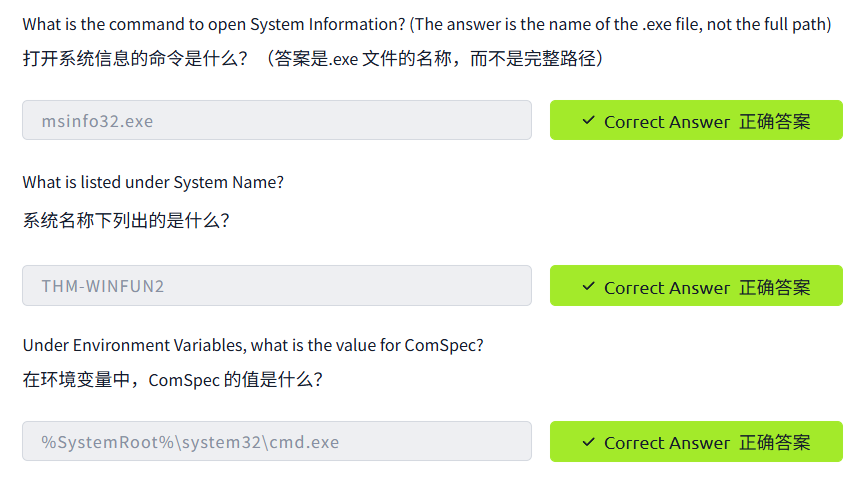
System Information
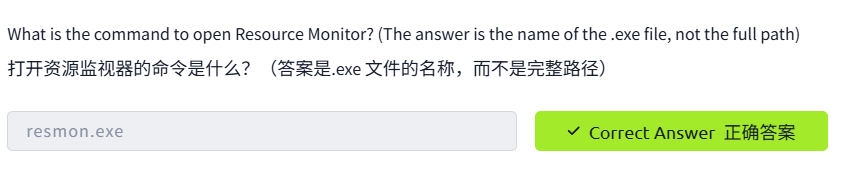
Resource Monitor
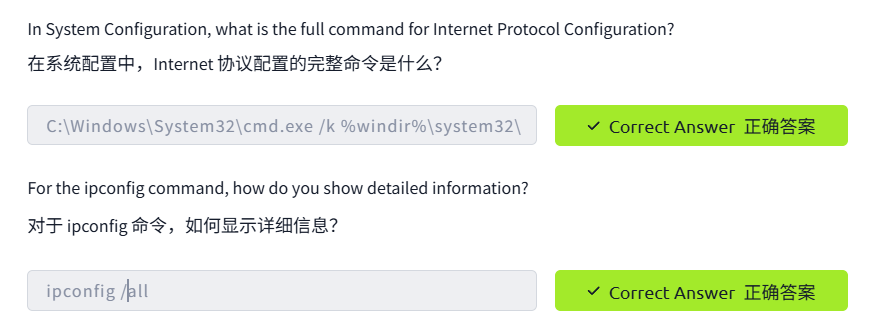
Command Prompt
Windows Fundamentals 3
Firewall & network protection
Device security

BitLocker
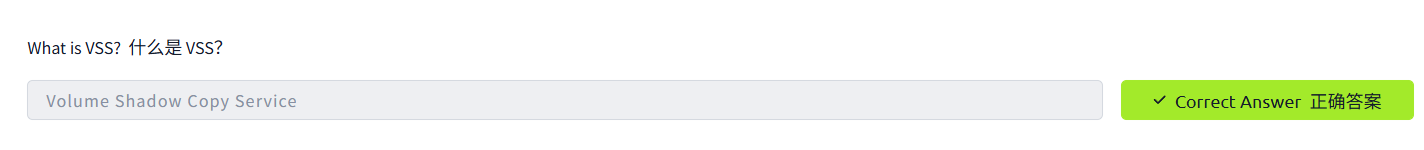
Volume Shadow Copy Service
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 再努力一点,她是不是就会回来!